Getting Started
First, we have to install the tool on our machine using the following command:
git clone https://github.com/Abdulraheem30042/Cl0neMast3r.git
Then we change directory to Cl0neMast3r by typing the following command:
cd Cl0neMast3r/
We find out that there are some requirements that need to be installed, so we execute the following command:
pip install -r requirements.txt
You should see something similar to the above screenshot when you successfully install the requirements.
Before starting the tool, we may need to change permission of the file by typing the following command:
chmod +x Cl0neMast3r.py
Then we start the tools by typing the following command:
python Cl0neMast3r.py
When the tool starts, your screen should look like the following:
We can see that it gives us various options such as adding a tool, find a tool among others.
We can start with adding a tool. In a previous post, I talked about SSLyze tool. Let’s say that we wanted to add the tool to our penetration testing tools.
Whilst Cl0neMast3r is running, to add the tool, we type
a
The tool asks us to provide the GitHub link of the SSLyze tool.
Then we enter the following link:
https://github.com/nabla-c0d3/sslyze
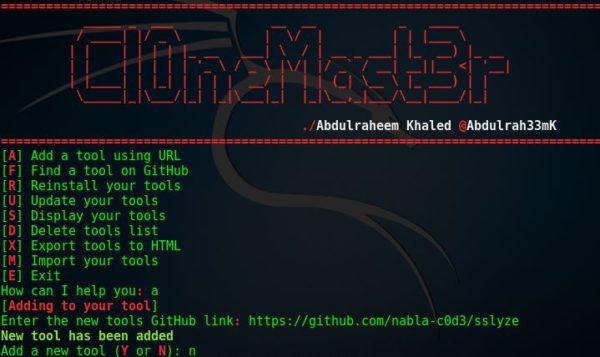
Then tool asks us if we want to add a new tool, if you want to add a new tool, you can type:
y
I don’t want to add a new tool, so I typed:
n
When the tool is successfully added, you should see the following message:
Then you type:
m
To return to the main page when asked by the tool.
As a verification measure, we want to make sure that the tool has been successfully added. So we type:
s
To display the list of our tools
If you successfully installed SSLyze, you should be able to see it in your list.
Your screen should look like the following:
In conclusion, as a penetration tester, you should have a toolbox to work with whilst conducting your ethical hacking assignment. This will help you to better scan, identify vulnerabilities and extract information during your engagement.







